This is infuriating that I continue to get this repeats of nine and more possible hack attempts from the same certain IP addresses blocked by Malwarebytes, which I get popups every time it happens. This is a snapshot from my logs after one has happened, and I also save text file logs of it.
From what I can tell, they appeared to be originating from Linode almost every time and when I tried to file complaints with them, they keep claiming it is a security researcher or something and end up doing nothing about it. I’m currently wondering what to do about this as I have a folder of so many save logs of it on my computer.


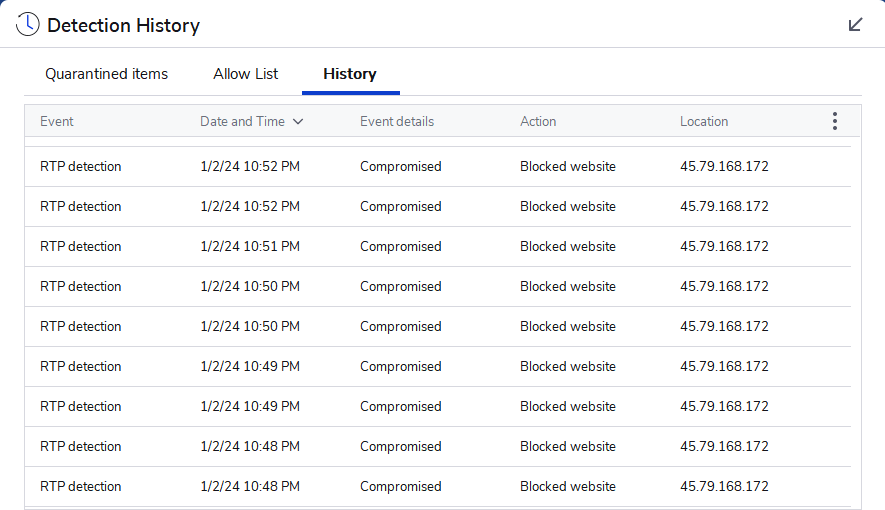
Not that I can tell, this is what shows up in the logs of just one of the hack or scan attempts.
Malwarebytes www.malwarebytes.com
-Log Details- Protection Event Date: 1/2/24 Protection Event Time: 10:48 PM Log File: f150648e-a9ea-11ee-8d8b-04d4c458e8f6.json
-Software Information- Version: 4.6.7.301 Components Version: 1.0.2222 Update Package Version: 1.0.79191 License: Premium
-System Information- OS: Windows 10 (Build 19045.3803) CPU: x64 File System: NTFS User: System
-Blocked Website Details- Malicious Website: 1
-Website Data- Category: Compromised Domain: IP Address: 45.79.168.172 Port: 6667 Type: Inbound
A quick search shows that IP is known for hacking type requests https://www.abuseipdb.com/check/45.79.168.172
I would check how your router is setup, as they should not be hitting your computer at all.
Port 6667 is a typical IRC port. It is sometimes used by remote access backdoors for command and control via a channel (chat room basically) on an IRC server, however, if that port isn’t forward OR you don’t have your PC set as the DMZ Host (you should never do this), then you probably have malicious software on your system.
If it isn’t forwarded, then your NAT would drop the packets and Malwarebytes would never see it because they wouldn’t be there. Malicious software can forward ports via uPNP and you should turn that off on your router or router/modem combo. It can also make it through if the connection is starting from inside of your network for TCP, which is the protocol that would be used for 6667 normally.